Application overview
Datto SaaS Defense is easy to use and navigate. Application features enable you to do the following:
- Access and investigate detailed threat information
- Send your organization an "alert" automatically when a malicious attack on a client's application is detected
- Create threat detection reports for your clients
- Monitor and configure client information
Datto Report Threat Application
A key component of Datto SaaS Defense is the Defense Report Threat add-in application for Microsoft Outlook. It enables client end users to notify you via Outlook when an email may have been incorrectly allowed or blocked by Datto SaaS Defense. The Defense Report Threat application is a convenient method for end users to request that you address the incident. When reporting an incident, the end user is required to identify the type of threat, such as unknown sender, extortion, or spam. For more information, see the Events page description.
Main menu
Each Datto Saas Defense page is accessed from the Main menu.
A description of each page is provided below.
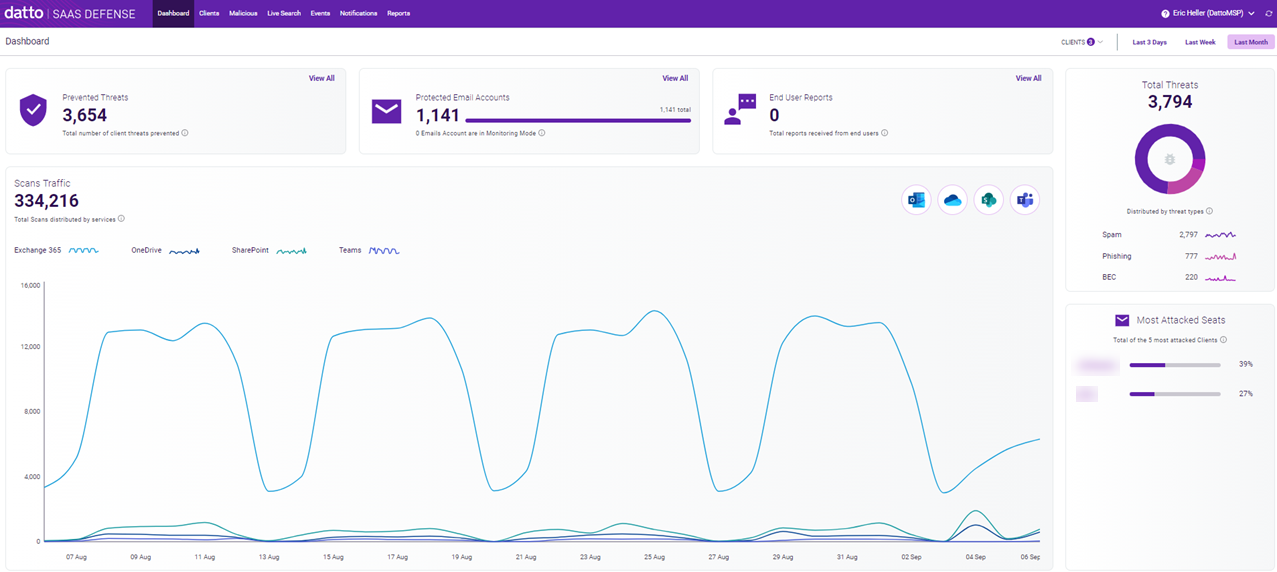
The Datto SaaS Defense Dashboard provides a useful and meaningful visual display of your organization's key platform information. The Dashboard allows you to quickly track your environment's product usage and effectively monitor threat prevention activity within your organization.
It includes six widgets (sections): Prevented Threats, Protected Email Accounts, End User Reports, Total Threats, Most Attacked Seats, and Scans Traffic.
See the article Datto SaaS Defense Dashboard.
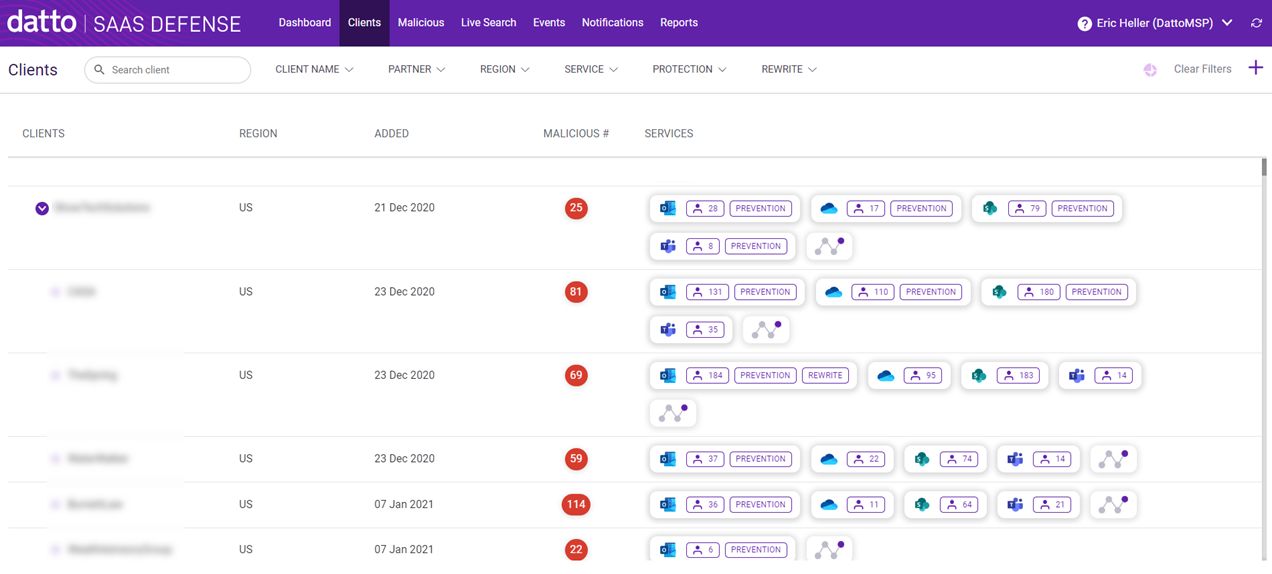
The Clients page provides access to client information such as the date you activated SaaS Defense for the client, the number of malicious attacks (if any) attempted on the client's Microsoft 365 applications, and the number of seats protected for each of those applications. Client management tools on this page allow you to:
- choose whether Datto SaaS Defense automatically blocks incoming threats or only flags threats allowing you to investigate further.
- create email and URL allowlists and blocklists.
See the article Managing Clients on the Clients page.
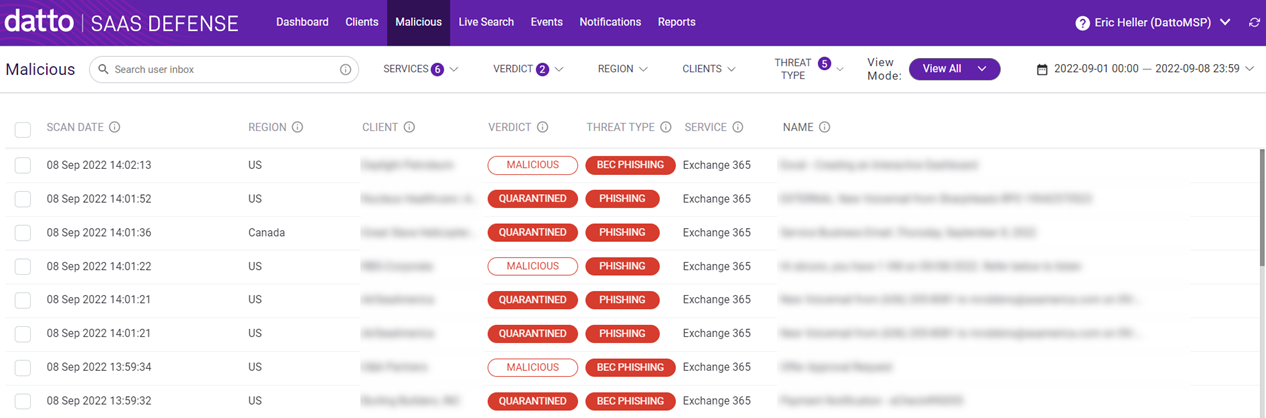
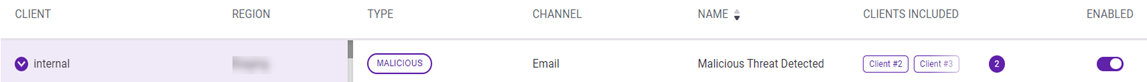
On the Malicious page, you can access detailed information concerning attempted attacks. Drilling into an attack record enables you to investigate specific attack data (artifacts) that helps you determine whether a malicious attack actually occurred.
See the article Analyzing threats on the Malicious page.
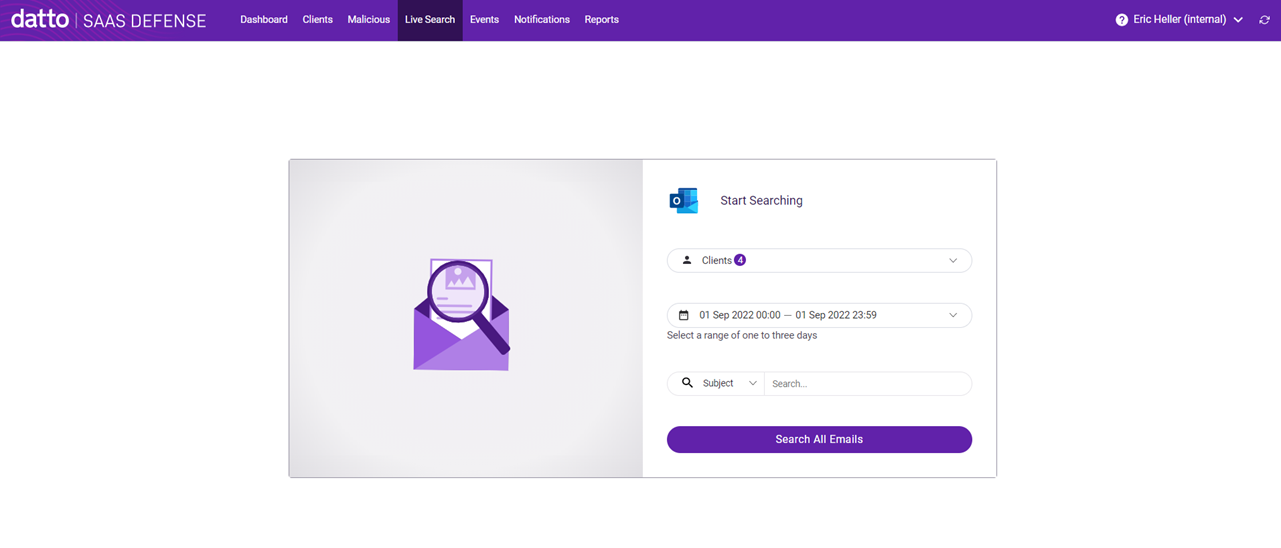
Maybe you'd like to analyze only the emails of clients who have been targets of a specific attack. Or, perhaps you need to investigate why a specific client's emails are being blocked. The Live Search feature enables you to search your clients' Exchange 365 mailboxes to find emails quickly and take action if necessary.
The Events page lists the records for which a client has determined an email was mishandled by Datto SaaS Defense. There are two situations where this may occur. In one situation, the client identifies an email as a security threat that should have been quarantined by Datto SaaS Defense, but it wasn't. In the other situation, an email was quarantined by Datto SaaS Defense but the client verifies it was not a threat. Therefore, the email should not have been quarantined.
To give your clients the ability to provide you with information related to these situations, you need to install the Datto SaaS Defense Report Threat Outlook add-in for each of your clients. A client sends the information via Outlook and it automatically populates on the Events page.
See the article Reviewing an incident report on the Events page.
Using the functionality on the Notifications page, you can create a custom message that the system automatically sends to alert you about a malicious attack or when an end user has reported a threat incident.
See the article Adding a notification on the Notifications page.
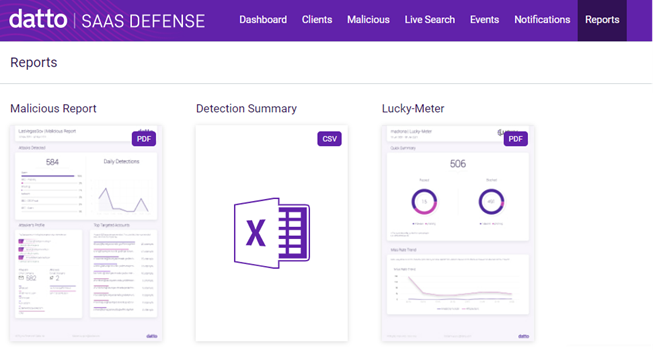
On the Reports page, you can create customized reports that provide a high-level view of the malicious traffic in your environment. You can simultaneously create multiple reports customized for each client. In addition, you can create reports analyzing your environment's vulnerability to threats.
See the article Creating reports on the Reports page.