Analyzing threats on the Malicious page
Information about security threats that have been identified by Datto SaaS Defense are conveyed on the Malicious page. You analyze the threat details on this page and can take action, if necessary.
Malicious page
When Datto SaaS Defense detects a security threat, it creates a detailed record of the threat that is listed on the Malicious page. 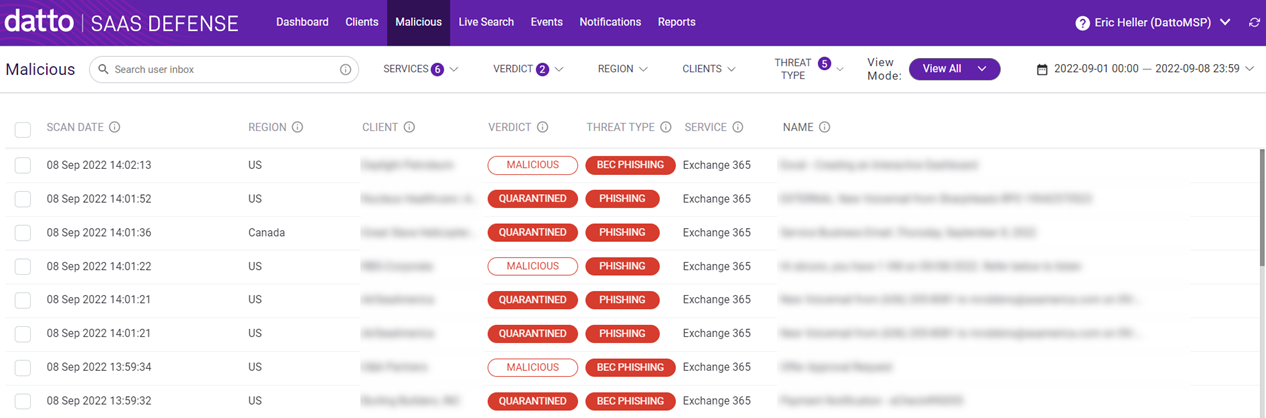
The Malicious page information is described in the table below.
| Column | Description |
|---|---|
| Scan Date | The date and time on which the record of the threat was created. |
| Client | The name of the client for which the threat was prevented. |
| Subject | The title Datto SaaS Defense assigned to the threat record. The value is assigned based on the application for which the threat was intended. For example, when a threat is intended for Exchange 365, the text used in the email's subject field is displayed in the Subject field. |
| From | The sender's email address. |
| Region | The region in which the client is located. |
| Verdict | The action taken by Datto SaaS Defense or by you to handle a malicious threat. Values are:
|
| Threat Type | The type of threat as determined by Datto SaaS Defense. See the article Types of threats prevented. |
| Service | The specific application that was scanned. |
IMPORTANT When an existing file in OneDrive or SharePoint is edited or replaced with a new version, SaaS Defense scans the document for malicious threats and looks for restricted content based on client policy. If the scan results in a quarantined verdict, but another user was using the existing document while the scan occurred, the document cannot be quarantined. Instead, the updates are made to the existing file, and a record is created on the Malicious page with a Malicious Verdict.
Releasing a quarantined email or file
The first column in the table includes a checkbox for each threat record. You can release an email or file that has been quarantined (Verdict = Quarantined) or restricted (Verdict = Restricted) by selecting the checkbox for the applicable record(s)and clicking Release. 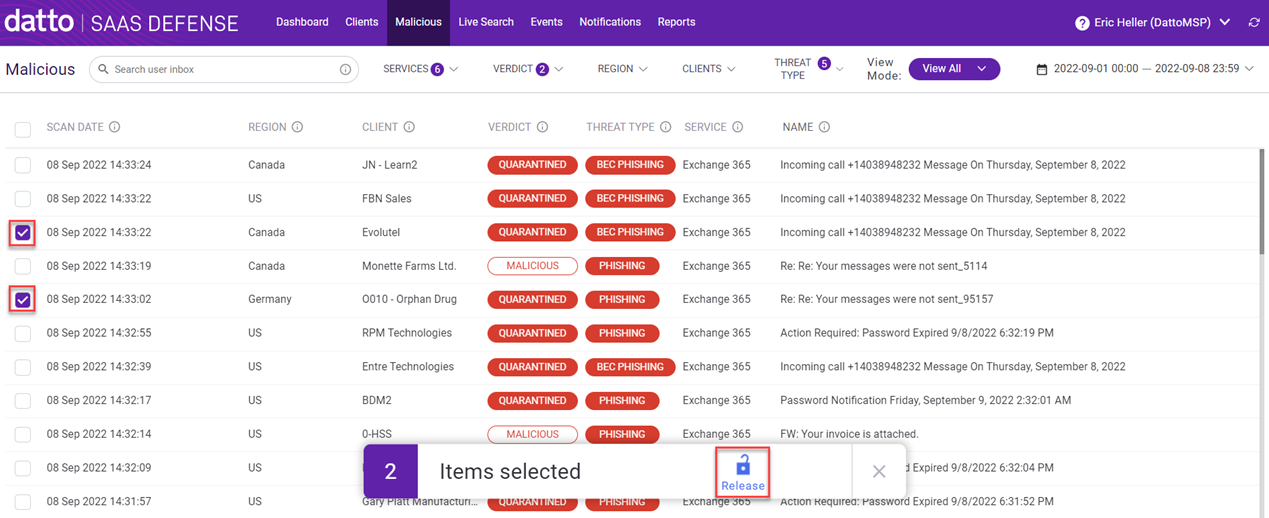
You will be prompted to confirm the release. 
Releasing a quarantined email delivers it to the intended recipient. A quarantined file that is released is available at its original location.
Content whose Verdict = Malicious cannot be released because it was not quarantined to begin with.
Malicious page toolbar
The Malicious page toolbar allows you to select filtering options to display only the threat records that match the options you select. 
Search box
You can use this search box to search for and display only the threat records for the email address you enter. A valid user inbox email address is required to conduct a search. 
The search box applies to the Exchange 365 and OneDrive services only. Therefore, one or both of these services are required to be selected in the Services filter.
NOTE Exchange 365 and OneDrive are among the services selected by default. You can use the Services filter to deselect and select services.
The results on the Malicious page don’t show the user inbox address. However, you can click a record to open the Verdicts & Info pane. The User Inbox address is displayed in the Scan Summary section (see the Verdicts & Info section below).
Filters
The table below describes each filter.
| Menu | Description |
|---|---|
| Services | Lists the services/applications available in your organization. |
| Verdict | Lists each verdict type. Options are:
|
| Region | Lists the regions for which your clients may be located. |
| Clients | Lists the names of each of your clients. |
| Threat Type | Lists each threat type. For more information about threat types, see the article Types of threats prevented. |
| View Mode | Provides options for grouping threat records:
|
| Date & time | Displays a calendar from which you can select a date and time range or select a specific option such as This Week, Last Month, etc. |
Verdicts & Info
The Verdicts & Info pane allows you to drill down into the artifacts of the security threat record you select. The information is divided into sections that vary based on the threat type determined by Datto SaaS Defense. However, the Header and Scan Summary sections are always populated regardless of threat type.
Header section
The Header section displays key words that summarize the attack data. In this example, a malware threat was sent by abpcabinets@bigpond.com via Exchange 365 and quarantined by Datto SaaS Defense. Also, there is the option to release the quarantined email. For malicious emails detected in Monitoring Mode, you have the option to quarantine the email.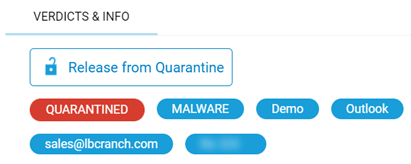
Scan Summary section
The Scan Summary section is located below the header section and includes customized information based on the threat type. The Scan Summary section for the malware threat example is shown below.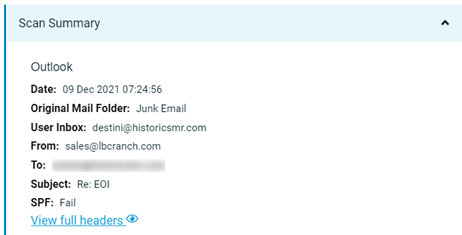
The following table describes the Scan Summary information for the malware threat.
| Information | Description |
|---|---|
| Date | The date on which the email was received by the folder indicated in the Original Mail Folder field. |
| User Engagement | Indicates if the user acted on the email. |
| Current Mail Folder | The current mail folder in which the email is located. |
| Original Mail Folder | The mail folder in the organization that first received the email. |
| User Inbox | The end user's mailbox address. |
| From | The Email address of the sender. |
| To | The Email address of the intended recipient. |
| Subject | The text the sender entered in the email's Subject field. |
| SPF | The Sender Policy Framework (SPF) status. SPF is an email authentication method used to verify the email sender with the sender's domain. |
| View Full Headers | A link to the email's complete header information. |
Scan Dynamics pane
The Scan Dynamics pane displays an interactive visual of the malicious attack. This is where you really dive into the artifacts to analyze the threat. Each artifact is represented by a labeled node. A red circle means Datto SaaS Defense has identified the artifact as malicious. Moving dots illustrate data flow to and from the artifacts.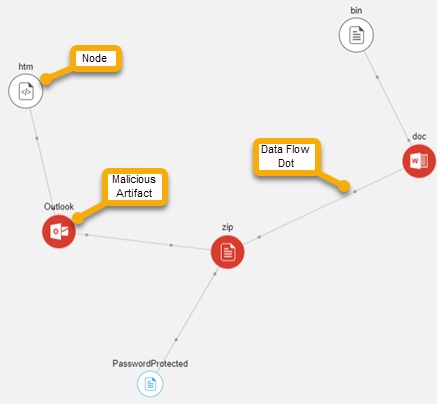
You can hover over a node to display basic information about the artifact. 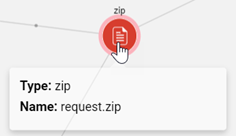
Clicking the node displays comprehensive information on the Details tab. 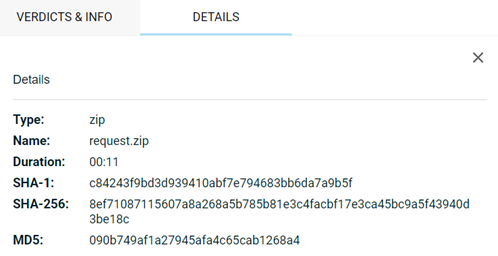
Continuing with the malware threat example, the Scan Dynamics image below shows the threat was received via Outlook. The email contained a malicious Excel (.xlsx) file. The Process Policy document includes the process Datto SaaS Defense performed to detect two instances of the attack. (EQNEDT32.EXE).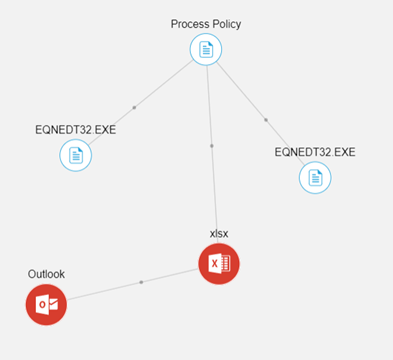
Analyzing a threat
Drilling into the details of an attack helps you determine the reason an email or file was blocked, which is valuable information you can provide to your client.
Perform the following steps to analyze a threat:
- Access the Datto SaaS Protection Status Overview page.
- For the applicable client, in the SaaS Defense Status column, click the link indicating the number of threats detected (in Prevention or Monitoring Mode).
- If desired, filter the Malicious page results. For more information, see the articles Filtering page results and Using the Calendar tool.
- Click anywhere on the desired record.
- In the Verdicts & Info pane, review the Header and Scan Summary sections.
- Review additional sections as necessary.
- Analyze the artifacts in the Scan Dynamics pane.
- To display basic artifact information, hover over the artifact.
- To display comprehensive artifact information, click the artifact.
- To quarantine an email or file that SaaS Defense has assigned a Malicious verdict:
- In the Header section, click Move to Quarantine.
- In the dialog box verifying you want to quarantine the email, click OK.
- In the dialog box confirming the email has been successfully quarantined, click OK.
- To release an email or file that SaaS Defense has Quarantined:
- In the Header section, click Release from Quarantine.
- In the dialog box verifying you want to release the email, click OK.
- In the dialog box confirming the email has been released, click OK.