Check SPF Spoofing per Domain configuration
This article describes the Check SPF Spoofing per Domain configuration. It also addresses the specific errors for which SaaS Defense disables the configuration for clients whose SPF record is misconfigured or is in its default state.
Check SPF Spoofing per Domain
The Check SPF Spoofing per Domain partner configuration is a policy that allows SaaS Defense to access and verify the SPF record of the email sender's domain. The configuration is enabled by default and it is recommended that it remains enabled.
With the Check SPF Spoofing per Domain configuration enabled, when a client receives an email, SaaS Defense verifies the following conditions:
- The domain from which the email was sent matches the client's domain.
- The specific server from which the email was sent is authorized in the domain's SPF record.
If either one of these conditions is not true, SaaS Defense considers this a definitive sign of email spoofing and blocks (prevention mode) or flags (monitoring mode) the email.
NOTE SaaS Defense accesses the SPF records of Microsoft Exchange clients only.
IMPORTANT It is essential that each of your client's has an SPF record created correctly for its domain. For more information about SPF records, see the article Creating a Sender Policy Framework record. For clients that will create the SPF record themselves, you can provide them with a PDF version of the article.
SPF record errors
With the Check SPF Spoofing per Domain configuration enabled, if a domain's SPF record is not configured correctly, SaaS Defense treats emails received from this domain as spoofing attempts. Therefore, depending on whether Datto SaaS Defense is operating in Prevention or Monitoring mode, it blocks or flags these emails, even though some of the emails may be legitimate. For every email sent by the domain, SaaS Defense continues to check the domain's SPF record even though it is still configured incorrectly and continues to treat emails sent by this domain, including those that are legitimate, as spoofing attempts.
Daily SPF record test
Datto SaaS Defense performs a daily SPF record test of the domains for all your clients. The purpose of the test is to verify that a valid SPF record exists for the domain. If a client has multiple domains, the test is performed for each domain. The daily test is considered a single test.
To prevent SaaS Defense from continuing to check an SPF record that is configured incorrectly, functionality has been implemented based on the results of the daily SPF record test. When a daily SPF record test fails due to one of the errors described below, the domain is automatically added to the client's Check SPF Spoofing per Domain configuration in the disabled mode. Consequently, SaaS Defense will not access and verify the SPF record of this domain.
IMPORTANT If you would like to prevent the Check SPF Spoofing per Domain configuration from being disabled even when the daily SPF record test fails, see the Always Use SPF in Spoof Trial section below.
| Errors | Description |
|---|---|
| Default SPF Record | This error means that the organization is using a third-party service to send emails on behalf of the organization, but the IP address of the third-party server is not configured in the organization’s default SPF record. This may cause SaaS Defense to treat an email sent by the third-party server as a BEC phishing attempt when the email may be legitimate. To fix this error: IMPORTANT Every organization that uses Microsoft Exchange has a default SPF record. The Default SPF Record error only occurs when using a third-party service whose IP address is not configured in the organization’s default SPF record. |
| SPFRecordNotFound | This error applies when one of the following occurs:
|
| SPFSyntaxError | This error means the SPF record contains syntax errors. To fix this error: |
| SPFTooManyDNSLookups | This error means the SPF record includes more than 10 SPF records from other domains or sub domains. The To fix this error: Reduce the number of |
| SPFIncludeLoop | This error means the SPF record includes an SPF record from another domain (or sub domain) but that domain includes the SPF record of the original domain, causing an endless loop. To fix this error: |
When the client fixes the condition that caused the test to fail, the SPF record will pass the next daily test and the client's Check SPF Spoofing per Domain configuration will automatically be re-enabled.
Notification email
At the conclusion of the daily test, if the Check SPF Spoofing per Domain configuration was disabled or enabled for any of your clients, you will receive one email that includes the information for each affected client. If the Check SPF Spoofing per Domain configuration was disabled, the email identifies each client and the reason the client's configuration was disabled.
Also, the email will identify the clients whose Check SPF Spoofing per Domain configuration was re-enabled as a result of fixing the SPF record.
You will not receive an email if there has not been a change to any client's SPF record since the last daily test was performed.
When you add a new client, the SPF record for the client's domain is included in the next daily test. If the new client's SPF record fails the test, you will receive an email that includes the information for all of your clients that failed that particular test, not just the information for the newly added client.
Always Use SPF in Spoof Trial
If you would like to prevent the Check SPF Spoofing per Domain configuration from being disabled even when the daily SPF record test fails, enable the Always Use SPF in Spoof Trial configuration. When the configuration is enabled, SaaS Defense will continue to check domain SPF records and take the appropriate action even if the SPF record is misconfigured. In addition, you will no longer receive a notification email with the daily SPF record test results.
When enabled for a specific client, it applies to all of the client's domains. Or, the Always Use SPF in Spoof Trial configuration can be configured globally.
To configure the Always Use SPF in Spoof Trial rule for a specific client:
- Hover over the applicable client record and in the far right column, click the Configurations icon.
X
- In the Account Configurations section, click Emails.
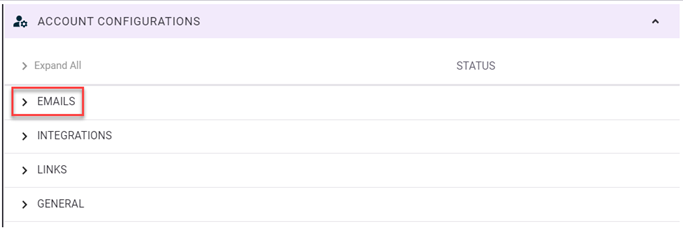
- For the Always Use SPF in Spoof Trial configuration, click the toggle in the Status column to enable it (button is on the right side in the Status column).
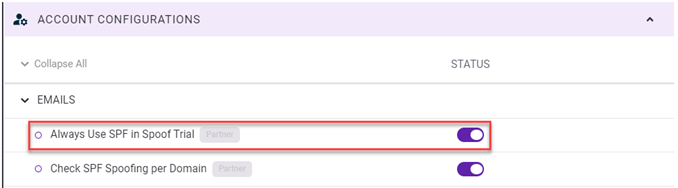
To configure the Always Use SPF in Spoof Trial rule globally:
- Hover over the applicable MSP record and in the far right column, click the Configurations icon.
- In the Global Configurations section, click Emails.
- For the Always Use SPF in Spoof Trial configuration, click the toggle in the Status column to enable it (button is on the right side in the Status column).